When news broke of Nicolás Maduro’s capture, a viral theory emerged: a mysterious internet routing anomaly days earlier had been a predictive sign of intelligence gathering. Dubbed 'The Internet "Glitch" That Predicted Maduro’s Capture', the event was quickly framed as state-sponsored "BGP shenanigans" by Venezuela’s government, setting the stage for the military operation.
The reality, according to Cloudflare, is far more mundane and much more embarrassing for Venezuela’s state-run infrastructure.
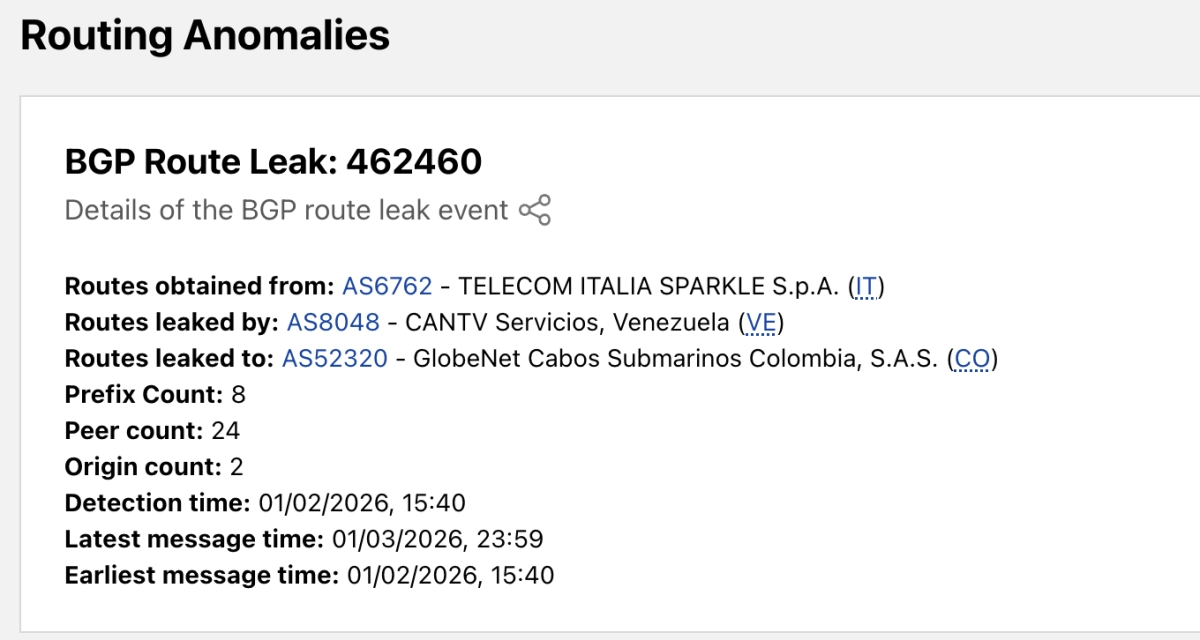
The anomaly in question was a Border Gateway Protocol (BGP) route leak observed on January 2, 2026, involving AS8048, the Autonomous System identifier for CANTV, Venezuela’s primary internet service provider. BGP is the fundamental routing protocol that directs traffic across the global internet. A route leak is essentially a network taking a wrong turn, propagating routing announcements beyond their intended scope.
In this case, CANTV, acting as a customer to two major transit providers (Italy’s Sparkle and Colombia’s V.tal GlobeNet), took routes learned from one provider and incorrectly advertised them to the other. This is a classic Type 1 hairpin leak, a violation of the "valley-free" routing rule that governs how traffic should flow between networks.
Cloudflare’s analysis, detailed on their blog, suggests this was not a sophisticated espionage attempt but rather a recurring technical failure. Since the beginning of December, CANTV has been the source of eleven such route leak events.
The Case Against Malice
If CANTV was attempting to perform a man-in-the-middle (MITM) attack to intercept traffic—as the initial theory suggested—they failed spectacularly. Cloudflare data shows that AS8048 heavily "prepended" its own AS number multiple times in the leaked advertisements. Prepending makes a route *less* attractive to other networks, effectively pushing traffic away from the path, the opposite of what a malicious actor would do.
Furthermore, the leaks began over twelve hours before the US military strikes in Venezuela. Cloudflare concludes that the most likely cause is simply poor technical practice: CANTV has "too loose of export policies" toward its providers, meaning routes belonging to its customers were accidentally redistributed upstream.
This incident highlights a critical vulnerability in global routing security. While the narrative around 'The Internet "Glitch" That Predicted Maduro’s Capture' was dramatic, the underlying problem is systemic. The internet still relies heavily on trust.
The solution isn't better political forecasting, but better technical standards. Cloudflare notes that this specific path-based anomaly would not have been prevented by RPKI (which only validates the origin of a route). Instead, the industry needs widespread adoption of the upcoming standard, Autonomous System Provider Authorization (ASPA). ASPA validates the path a route takes, ensuring that a provider like CANTV cannot incorrectly advertise customer routes to another provider, regardless of their internal policy errors. Until ASPA is mandatory, these "glitches" will continue to be a common, if sometimes politically charged, byproduct of a trusting internet architecture.