The internet is bracing for a tidal wave of AI agents, and traditional web defenses are proving inadequate. Cloudflare, in collaboration with industry players, is pushing for a new standard: the bot authentication registry. This system, coupled with advanced anonymous credentials, aims to provide website operators with fine-grained control over automated traffic while safeguarding user privacy, fundamentally reshaping how we manage the web's growing AI population.
The Web's New Gatekeepers: Identifying and Managing AI Agents
The internet is on the cusp of a profound transformation, driven by the proliferation of AI agents. Soon, asking your phone to "order a pizza" won't just involve a human clicking through menus; an AI agent will orchestrate the entire process, browsing websites, making selections, and even handling payments on your behalf. This shift, as detailed in recent proposals from Cloudflare's Thibault Meunier, Maxime Guerreiro, and others, presents a monumental challenge for website operators: how do you manage a surge of automated traffic that moves at datacenter speeds, without inadvertently blocking legitimate users?
Traditional methods of web traffic management—relying on IP addresses, user agents, or even CAPTCHAs—are quickly becoming obsolete. When an AI platform like Amazon Bedrock AgentCore sends requests on behalf of thousands of users, blocking its IP range to mitigate an attack means shutting out everyone. The problem is twofold: identifying the *source* of automated traffic with trust, and then managing its *behavior* without compromising individual user privacy.
Enter Web Bot Auth, a protocol proposal introduced earlier this year that allows bots and agents to cryptographically sign their requests. This moves beyond brittle identification methods to more trustworthy authentication. Companies like Vercel, Shopify, and Visa are already implementing it, marking a crucial first step. But cryptographic keys, much like IP addresses, are pseudonymous. How does a website operator, especially one without the scale of a major CDN, discover the public keys of the myriad bots and agents interacting with their site?
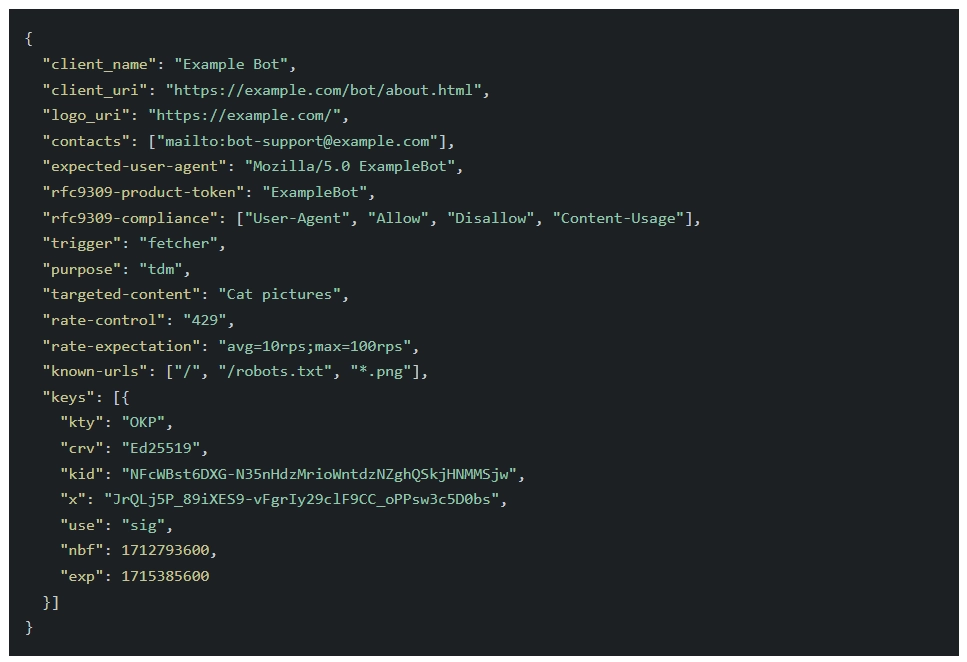
This "discovery problem" is precisely what the "bot authentication registry" aims to solve. Cloudflare proposes a registry format: a simple list of URLs where bot operators host their public keys and associated metadata. Think of it like an advanced `robots.txt` or a curated list of trusted IP ranges, but for cryptographic identities. Anyone can maintain and host these lists, fostering an open ecosystem of curators. Cloudflare itself plans to offer one of the first instances, providing a foundational reference for others.
The registry isn't just a list of keys; it's complemented by a "signature-agent card" format. This extends the standard JWKS directory (RFC 7517) with crucial metadata. Imagine an old-fashioned contact card, but for a bot: it includes the operator's name, a contact method, a logo, expected crawl rates, purpose (e.g., "academic research," "search agent"), and even targeted content. This rich information allows website operators to make informed decisions beyond a simple allow/deny. For instance, Cloudflare requires a contact method for verified bots, ensuring a channel for communication if issues arise.
This infrastructure is already seeing real-world adoption. Amazon Bedrock AgentCore, for example, is transitioning its AgentCore Browser service to use customer-specific keys, moving away from a monolithic signing key. This means Cloudflare and other origin protection services will soon be able to validate signatures from individual AgentCore customers, rather than just AgentCore as a whole, without identifying individual users.
Anonymous Credentials: The Privacy Layer for Bot Management
While the bot authentication registry provides a robust way to *identify* agents and their operators, it doesn't solve the problem of managing individual agent *behavior* without compromising user privacy. If an AI agent platform is sending millions of requests, and a few malicious users on that platform are causing issues, simply blocking the platform's registered key would punish all honest users. This is where anonymous credentials (ACs) come into play.
Anonymous credentials, currently under development at IETF, represent the next evolution of privacy-preserving security mechanisms, building on the foundation of Privacy Pass. The core idea is to allow website operators to enforce policies like rate-limiting or blocking malicious users, without ever having to identify or track individual users across requests.
The limitations of existing Privacy Pass implementations, which often rely on blind signatures, highlight the need for ACs. Blind signatures can be costly in terms of communication (0.5KB per request), struggle with per-origin rate-limiting (a token redeemed at one site can't be unlinkably redeemed at another), and lack revocation capabilities (once issued, a token remains valid).
Anonymous credentials address these shortcomings. They offer "sublinear complexity" for issuance (signing 10 attributes is cheaper than 10 individual signatures), "late origin-binding" (linking a token to an origin *after* issuance), "multi-show" capabilities (deriving multiple single-use tokens from one issuance), and "expiration distinct from key rotation" (tokens can expire independently of the issuer's cryptographic key). Crucially, ACs allow for "partial statements," meaning a client can prove possession of a credential and its attributes without revealing the entire message, thus preserving privacy.
Imagine a scenario where an AI platform issues a credential to a user, which includes a counter for how many requests they can make. When the user's agent makes a request, it presents the credential, proving it has a valid counter greater than zero, and the server decrements the counter, issuing a new credential for the updated value. The magic here is that this process happens in a way that prevents the server from linking multiple presentations by the same client, even though it's managing a counter. This is a significant leap beyond simple blind signatures, which would require the counter to be handled in plaintext, creating a privacy risk.
The combination of a transparent, open "bot authentication registry" for trusted identification and the privacy-preserving power of "anonymous credentials" for fine-grained control marks a pivotal moment for the internet. As AI agents become ubiquitous, these technologies offer a path to a more secure, manageable, and private web, ensuring that the benefits of AI automation don't come at the cost of user experience or fundamental privacy rights. It's a complex dance between visibility and anonymity, and Cloudflare, alongside its partners, is leading the charge to choreograph it for the AI era.